It ought to be described that MD5 just isn't perfect which is, in actual fact, acknowledged to become vulnerable to hash collisions. Hash collisions take place when unique parts of data make the same hash value, undermining the basic principle that each one of a kind piece of details need to produce a uniquely identifiable hash consequence.
Password Storage: Numerous Internet sites and programs use MD5 to shop hashed versions of person passwords. When buyers produce their accounts, the program generates an MD5 hash in their passwords and stores it inside a database.
The MD5 hash algorithm authenticates messages by creating a one of a kind identifier or “digital fingerprint” for a file. It then verifies this exceptional fingerprint when the message is obtained. This fingerprint is often known as a hash price or checksum.
MD5 can be a cryptographic hash functionality which is no more thought of Protected For lots of applications. Figure out why and what to employ rather.
Collision Attack Vulnerability: MD5 is at risk of collision attacks. Collision takes place when two separate inputs make the identical hash benefit. Researchers have confirmed viable collision attacks on MD5, which implies attackers can purposefully create numerous inputs resulting in the exact same MD5 hash output. The integrity and security of programmes jeopardise hash features for info identification.
A 12 months later on, in 2006, an algorithm was printed that made use of tunnelling to locate a collision within just one particular minute on one notebook computer.
MD5 is usually used in digital signatures. Much like how a Bodily signature verifies the authenticity of a document, a digital signature verifies the authenticity of digital facts.
All of it is determined by your certain wants and situations. So, consider some time to know Every of these alternate options in advance of determining which a person to adopt for the hashing requirements.
The Public Important in the receiver is accustomed to encrypt the plaintext because of the sender though the Non-public Key of the receiver is used to decrypt the encrypted message and consequently could be decrypted o
Dividing the Concept into Blocks: The padded concept is split into 512-little bit blocks that can be additional processed with the algorithm. If your information is fewer than 512 bits, it is considered just one block.
Checksum generation. MD5 is accustomed to make checksums for details blocks or data files. These checksums tend to be used in software program distribution, exactly where developers offer an MD5 hash so customers can verify the downloaded file is total and unaltered.
While contemporary cryptographic algorithms like SHA-256 have superseded MD5 on account of its vulnerability to collision assaults, it still remains important in knowledge foundational details security methods and holds historical relevance in the event of cryptographic approaches.
MD5 hash can be a cryptographic protocol that verifies the authenticity of documents despatched involving products—but could it be a match for technology these days?
even though it However lacks strength in more info today's context, the place details breaches have become significantly far more subtle, MD5 has undeniably been foundational in creating Superior cryptographic mechanisms.
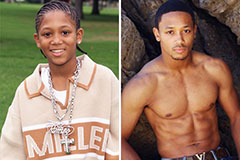 Romeo Miller Then & Now!
Romeo Miller Then & Now! Mackenzie Rosman Then & Now!
Mackenzie Rosman Then & Now! Gia Lopez Then & Now!
Gia Lopez Then & Now!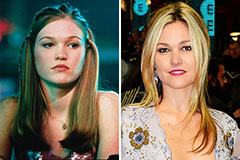 Julia Stiles Then & Now!
Julia Stiles Then & Now! Richard Dean Anderson Then & Now!
Richard Dean Anderson Then & Now!